What is OWE and why do we need it ?
In few past years, we have heard of a lot of situations in which the Open and WPA2 pre-shared key networks were cyber attacked and easily compromised.
Coffee shops, restaurants and many other public venues still use captive portal which in majority is open SSID’s, which means the data over the air is unencrypted.
OWE was introduced to address the issues on open authentication in 802.11 connection which resulted data transport in cleartext.
With OWE, the client and AP perform Diffie-Hellman key exchange during the time of association and use the resulting pairwise master key (PMK), which then is used during the 4-way handshake to protect the data in the 802.11 connection from being sniffed.
One thing to keep in mind though, from an open SSID prospective, the user still remains unauthenticated, which means administrator still doesn’t know the identity of the user, but the data traffic that passes through after establishing a wireless connection remains encrypted (unlike the legacy open SSID).
This is completely transparent to the users, which means everything remains the same from a user experience. Like the previous version of open SSID, they see an open network, they connect in just one click (no username and password), and the connection type now becomes encrypted.
What changed ? How is the traffic now encrypted ?
OWE uses Diffie-Hellman key exchange to establish a shared secret between two parties. It is primarily used as a method of exchanging cryptography keys for use in symmetric encryption algorithms like AES.
Detailed explanation of cryptography and Diffie-Hellman (DH) can be found here
Here are some detailed technical explanation with packet capture snippets done using Aruba devices (controllers and Access Points).

Wireless controllers/AP’s supports OWE (enhanced security) in below forms,
- OWE (without PMK Caching)
- OWE (with PMK Caching)
- OWE Transition Mode
My testings/pcaps are gathered using Aruba Devices.
OWE (without PMK caching):

While using this method, the 802.11 beacon, probe response, and authentication request or response frames are generic, but the association request or response are specific.
Aruba advertises support for OWE by using an AKM suite selector for OWE (00-0F-AC:18) in all beacons and probe response frames.
Protected Management Frames (PMF) is required to be set (MFPR=1).
Authentication request and authentication response use open authentication.
A client that wishes to perform data encryption in an open Wi-Fi network that uses OWE, indicates its capability in the AKM field of the 802.11 association request with PMF set to 1 (MFPR=1).
The DHPE (Diffie-Hellman Parameter Element) contains group and the Diffie-Hellman public Key from the client.
ArubaOS supports Diffie-Hellman Group 19, a 256-bit Elliptic Curve group.

Aruba AP’s includes the OWE AKM and DHPE in the 802.11 association response after agreeing to enhanced open with PMF field required (MFPR=1). The DHPE contains group and the Diffie-Hellman public key from ArubaOS.
If ArubaOS does not support the group indicated in the received 802.11 association request, it responds with an 802.11 association response having the status code 77.
A status code 77 indicates unsupported finite cyclic group.
After completing the 802.11 association, PMK and its associated PMKID are created. AP’s then initiates a 4-way handshake with the client using the generated PMK. The result of the 4-way handshake is the encryption key to protect bulk unicast data and broadcast data between the client and ArubaOS.
Sample OWE Beacon Frame – showing AKM and MFPR=1


The BSS Table on Aruba Controller shows the E Flag which indicates “Enhanced Open (OWE) BSS without Transition mode”

OWE (with PMK Caching)

With the support of PMK caching for OWE, the AP can cache the PMK for a certain amount of time. If a client wishes to do OWE with PMK Caching, it includes PMKID in its 802.11 association request in addition to OWE AKM, its DHPE and PMF required(MFPR=1).
If Controller/AP platform has cached the PMK identified by that PMKID, it includes the PMKID in its 802.11 association response but does not include a DHPE.
Otherwise, AOS-WLAN ignores the PMKID and proceeds with normal OWE 802.11 association response by including a DHPE.
The 4-way handshake is initiated after that.
OWE Transition Mode
OWE transition mode enables a seamless transition from Open unencrypted WLAN connections without impacting the end user experience. It provides the ability for OWE and non-OWE clients to connect to the same configured OWE VAP.
802.11 beacon and probe response frames from the OWE BSS include an OWE Transition Mode IE to encapsulate the BSSID and SSID of the Open BSS.
The beacon frame from the OWE BSS indicates OWE in RSNE.
802.11 beacon and probe response frames of the Open BSS include an OWE Transition Mode IE to encapsulate BSSID and SSID of the OWE BSS.
With Aruba devices, when transition mode is enabled, it broadcasts 2 different SSID’s, one for OWE capable devices only and other one for non-OWE capable (older) devices.

The BSS Table on Aruba Controller shows the flags o and O.
O = Enhanced-open BSS with transition mode; o = Enhanced-open transition mode open BSS.
OWE OPEN – Beacon Frame

Legacy OPEN – Beacon Frame
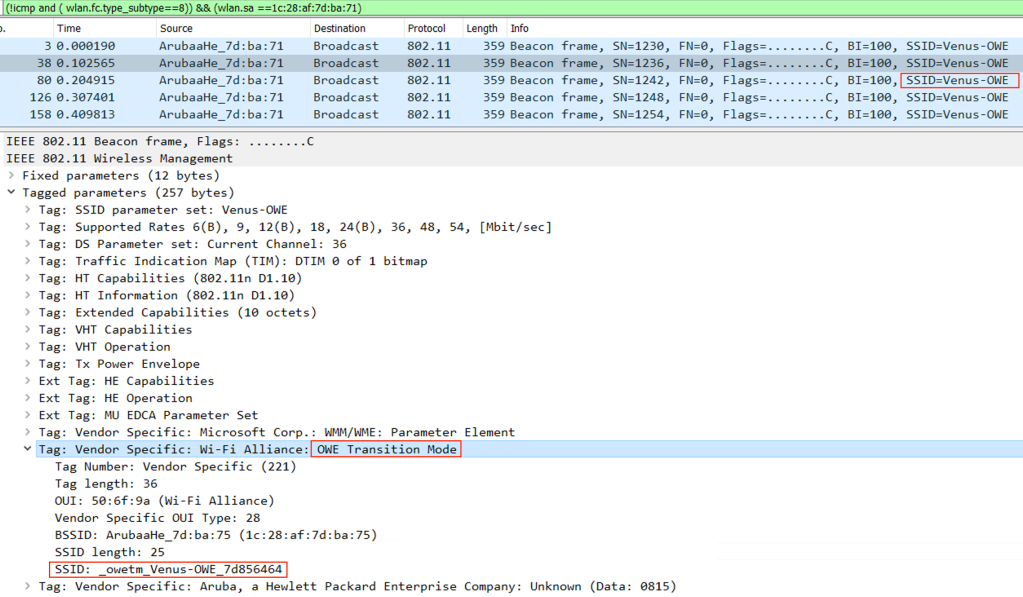
On an OWE capable device, we can see 2 SSID’s with the same name

On a non-OWE capable device, we can see only see one SSID

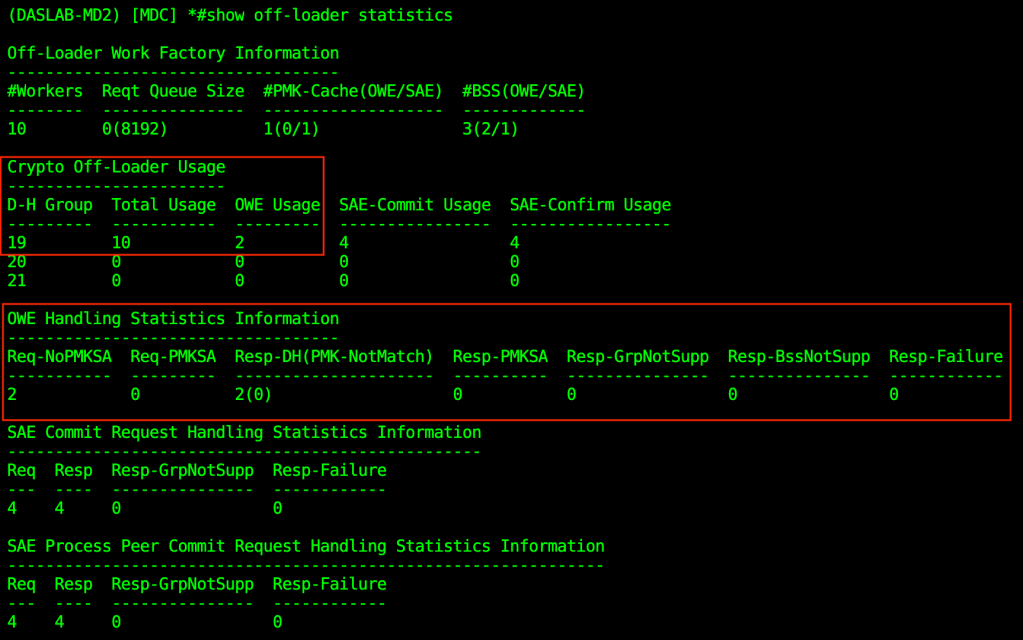
Aruba OWE stats information